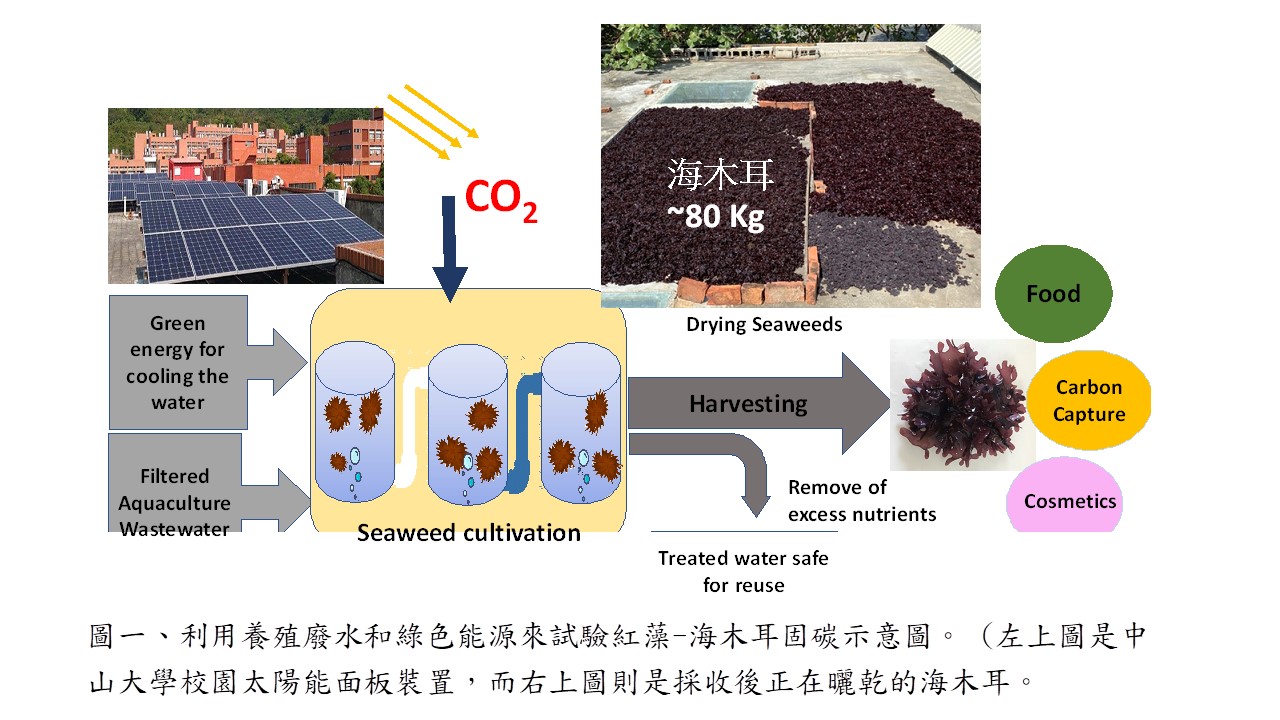
| Technical Name |
4G/5G多媒體系統之資安弱點檢測與威脅防護 |
| Project Operator |
National Yang Ming Chiao Tung University |
| Project Host |
李奇育 |
| Summary |
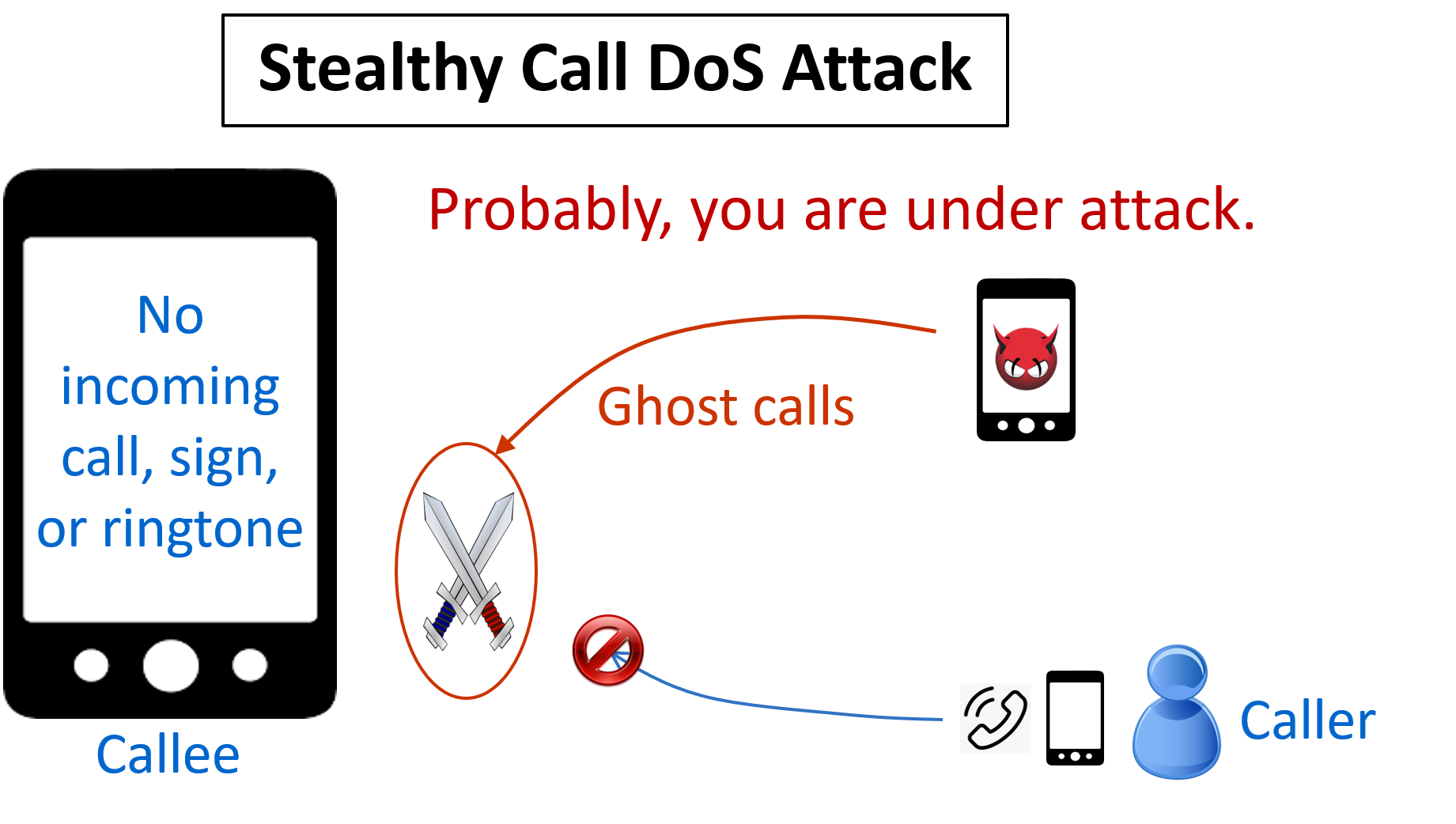
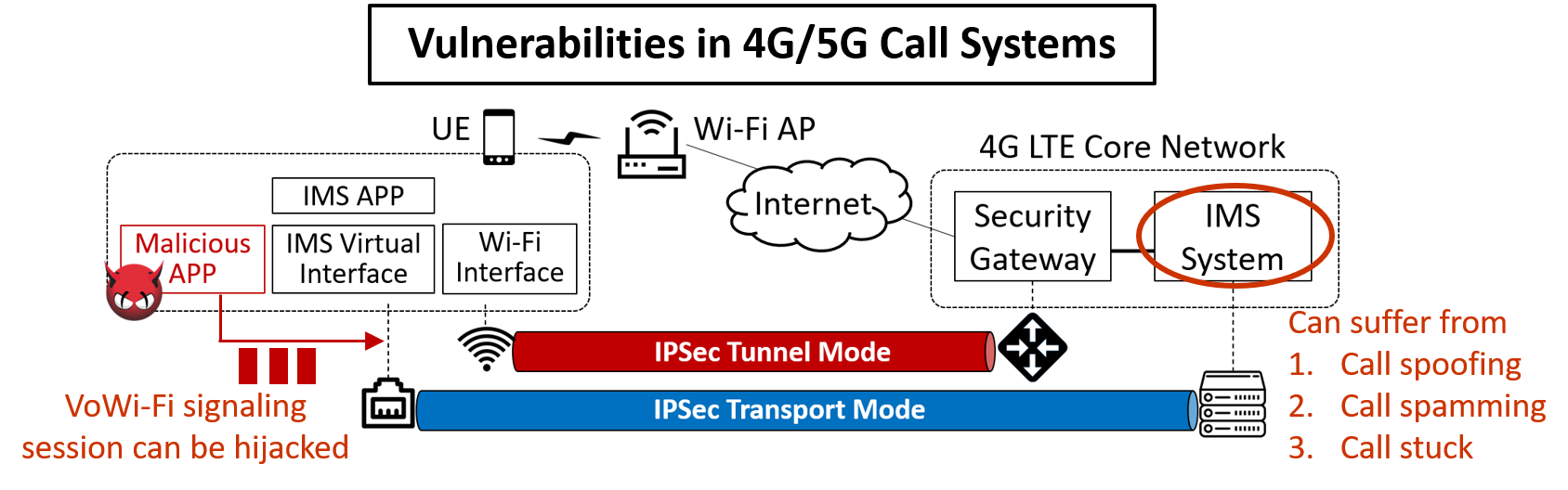
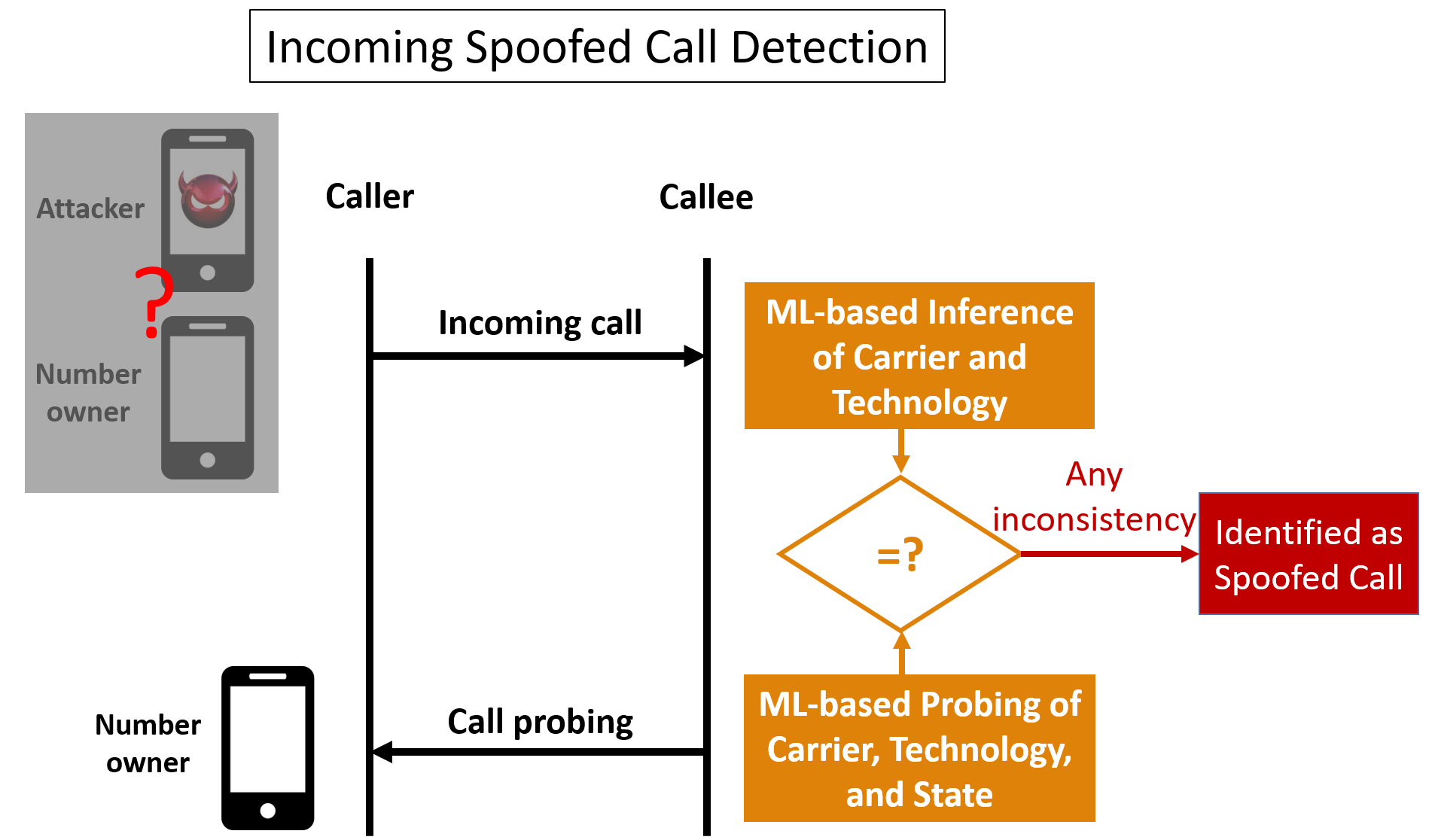
We develop a vulnerability detection module to identify three important security vulnerabilities in the IMS system that supports 4G/5G multimedia services. We have validated them in 4 carriers from TaiwanU.S. using smartphones from 7 brands,shown that they can be exploited to launch a stealthy call DoS attack, a social engineering attack with ghost calls,a call ID spoofing attack. Moreover, attackers can detect attackable users using an AI technique with only the users' phone numbers. We finally propose solutionsdevelop an AI-based technique of call ID spoofing detection. |
| Technical Film |
|
| Scientific Breakthrough |
"We are the first group in the world to have four breakthrough contributions below.
1. We developed a vulnerability detection module to identify four important security vulnerabilities in call state machine, call management, call ID verification,call information leakage, respectively, from the IMS system.
2. We validated those vulnerabilities in 4 carriers from TaiwanU.S. using smartphones from 7 brands.
3. We proposed solutionsvalidated their effectiveness experimentally.
4. We developed an AI-based technique of call ID spoofing detection, which can do detection at run time." |
| Industrial Applicability |
The security threats identified by our developed vulnerability detection module generally exist in global 4G/5G cellular network systems. The module can assist cellular network standards, carriers,telecom/phone vendors in detectingaddressing the security vulnerabilities of 4G/5G cellular networksmultimedia services. We have contributed the result to CHT, TTC, NCC,GSMA. The global 4G/5G IMS systems can thus benefit. We will start to promote the vulnerability detection moduleAI-based technique of call ID spoofing detection to the telecom industry. |
| Matching Needs |
天使投資人、策略合作夥伴 |
| Keyword |
5G IMS Security DoS Vulnerability detection Machine learning Call ID spoofing Security threat detection Mobile communication Security protection |