| Technical Name | Cyber Security Vulnerabilities Alert System Based on Information from Twitter and CVE | ||
|---|---|---|---|
| Project Operator | Taiwan Information Security Center at National Chung Hsing University | ||
| Project Host | 廖宜恩 | ||
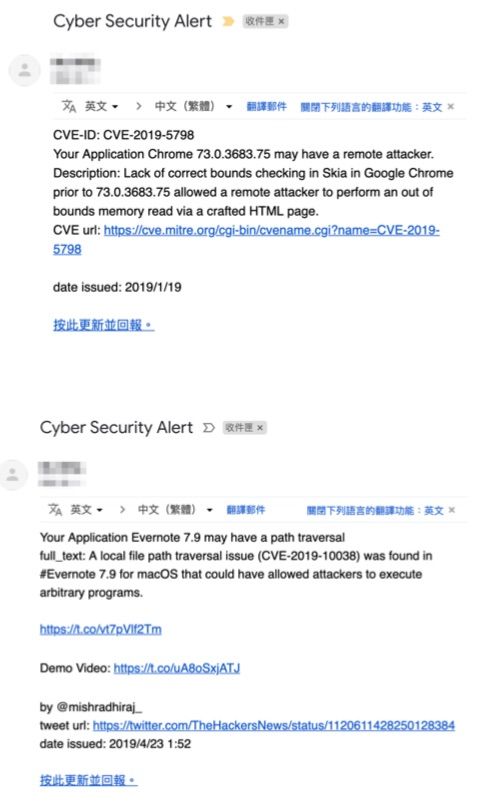
| Summary | The proposed system uses Convolutional Neural Networks (CNN) and Bidirectional Long Short-Term Memory (Bi-LSTM) to analyze the tweets by cyber security experts and the information from Common Vulnerabilities and Exposures (CVE) on an hourly basis and automatically check the system profile including firmware, OS, and application software for possible vulnerabilities. It will send alert messages to system administrator for taking appropriate actions to avoid zero-day/N-day attacks once potential vulnerabilities are found. |
||
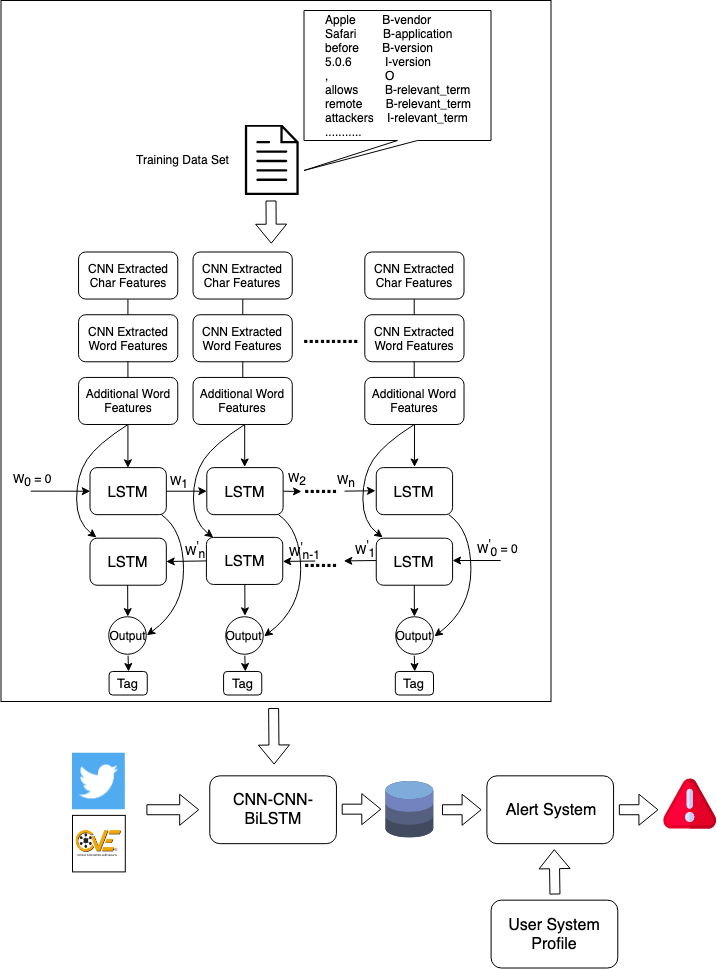
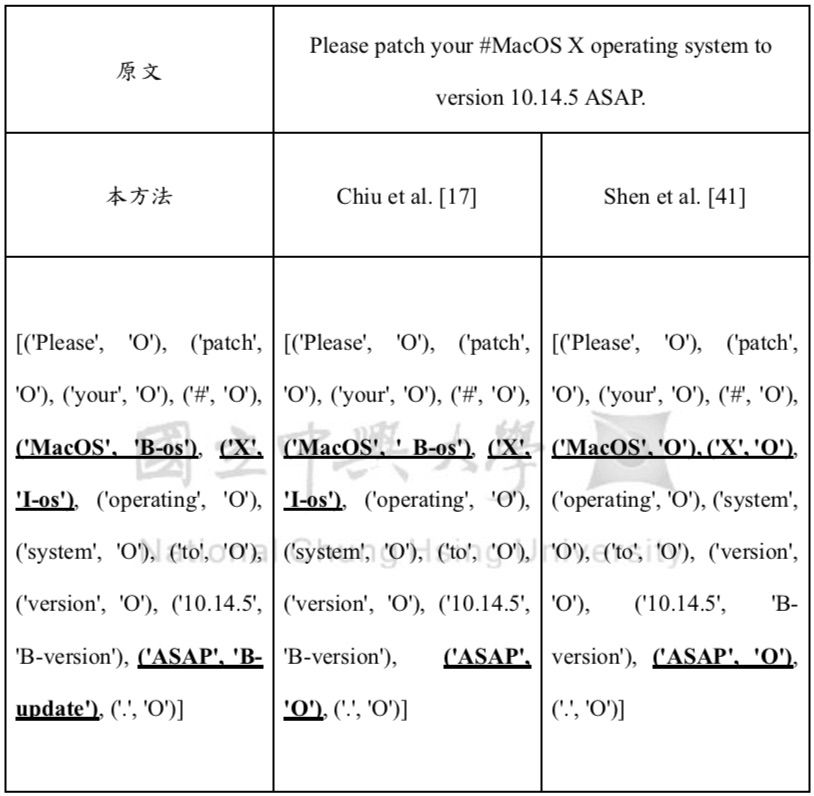
| Scientific Breakthrough | The proposed system uses CNN-CNN-BiLSTM to analyze the tweets by cyber security experts and the information from Common Vulnerabilities and Exposures (CVE) on an hourly basis and automatically check the system profile including firmware, OS, and application software for possible vulnerabilities. It will send alert messages to system administrator for taking appropriate actions to avoid zero-day/N-day attacks once potential vulnerabilities are found. The experimental results show that the proposed method has above 95% in Precision, Recall, and F1-measure for named entity recognition while the other two methods have about 89% and 85%, respectively, in all metrics. |
||
| Industrial Applicability | Using hourly accesses to the tweets by cyber security experts and the information from CVE as cyber security information source, the proposed system can automatically check the system profile including firmware, OS, and application software for possible vulnerabilities. It will send alert messages to system administrator for taking appropriate actions to avoid zero-day/N-day attacks once potential vulnerabilities are found. Therefore, the system has great potential of applicability because in 2018, 76% of successful attacks on organization endpoints were zero-day according to the Ponemon Institute’s 2018 State of Endpoint Security Risk report. |
||
| Keyword | Deep Neural Network Convolutional Neural Network Bi-LSTM Named Entity Recognition Cyber Security Vulnerability Twitter CVE 0-day attack N-day attack Vulnerabilities Alert System | ||
- a2730046@hotmail.com
other people also saw