| Technical Name | Security Testbed for Commercial IoT Devices Using Firmware Inspection and Hardware Emulation | ||
|---|---|---|---|
| Project Operator | Taiwan Information Security Center of National Taiwan University of Science and Technology | ||
| Project Host | 鄭欣明 | ||
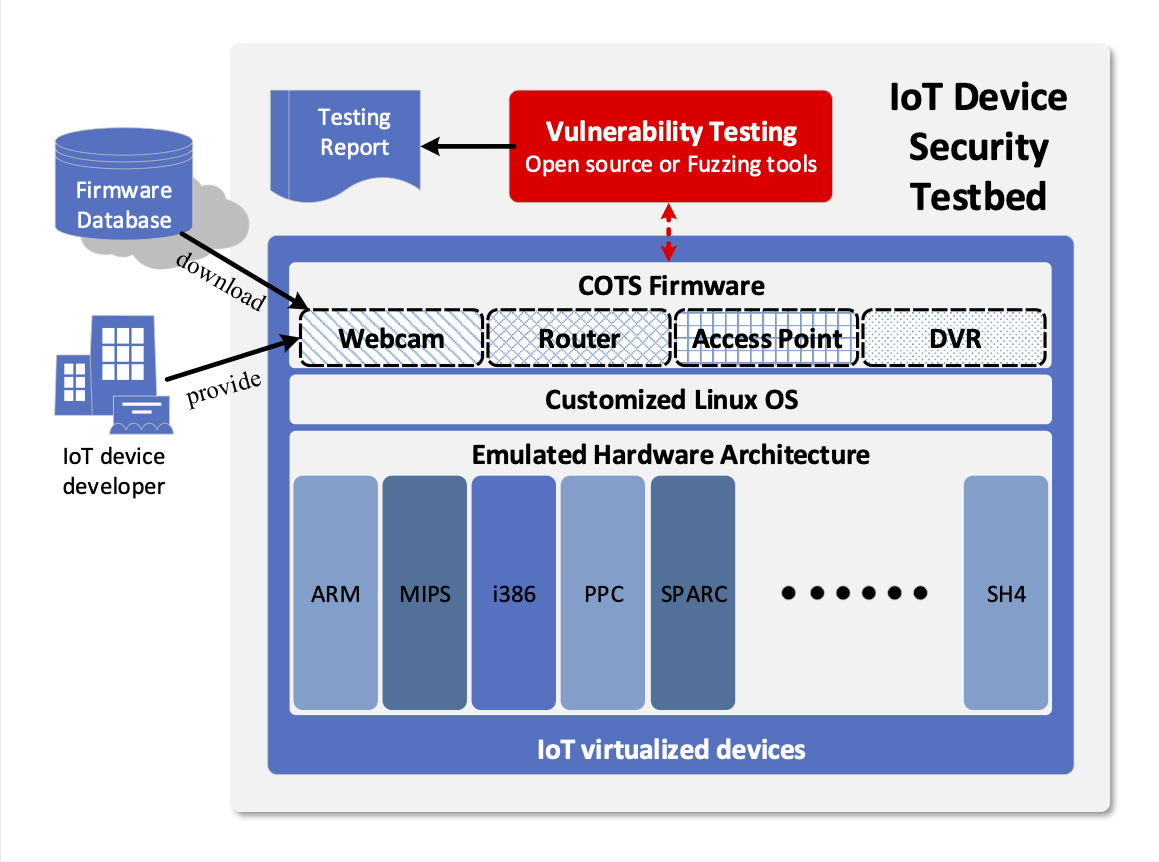
| Summary | When we examine COTS IoT devices with various kinds of hardware architectures, we need to connect the IoT devices with a particular security tester physically using debug interface, which is inconvenient, unscalable, and inefficient. To resolve this issue, we build an automatic IoT security testbed, which operates firmware of COTS IoT devices in the compatible system with emulated IoT architectures. |
||
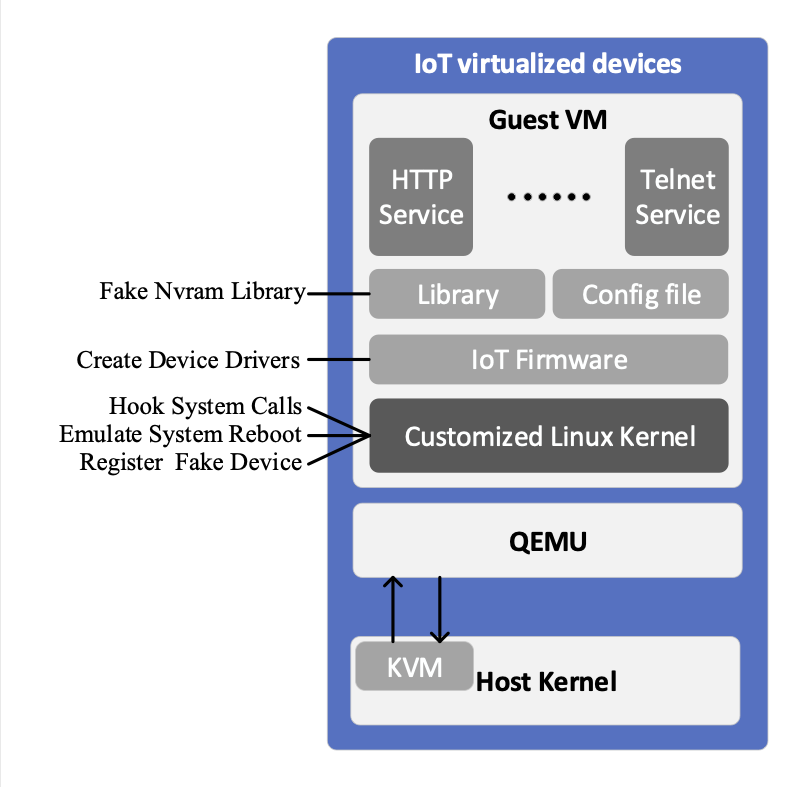
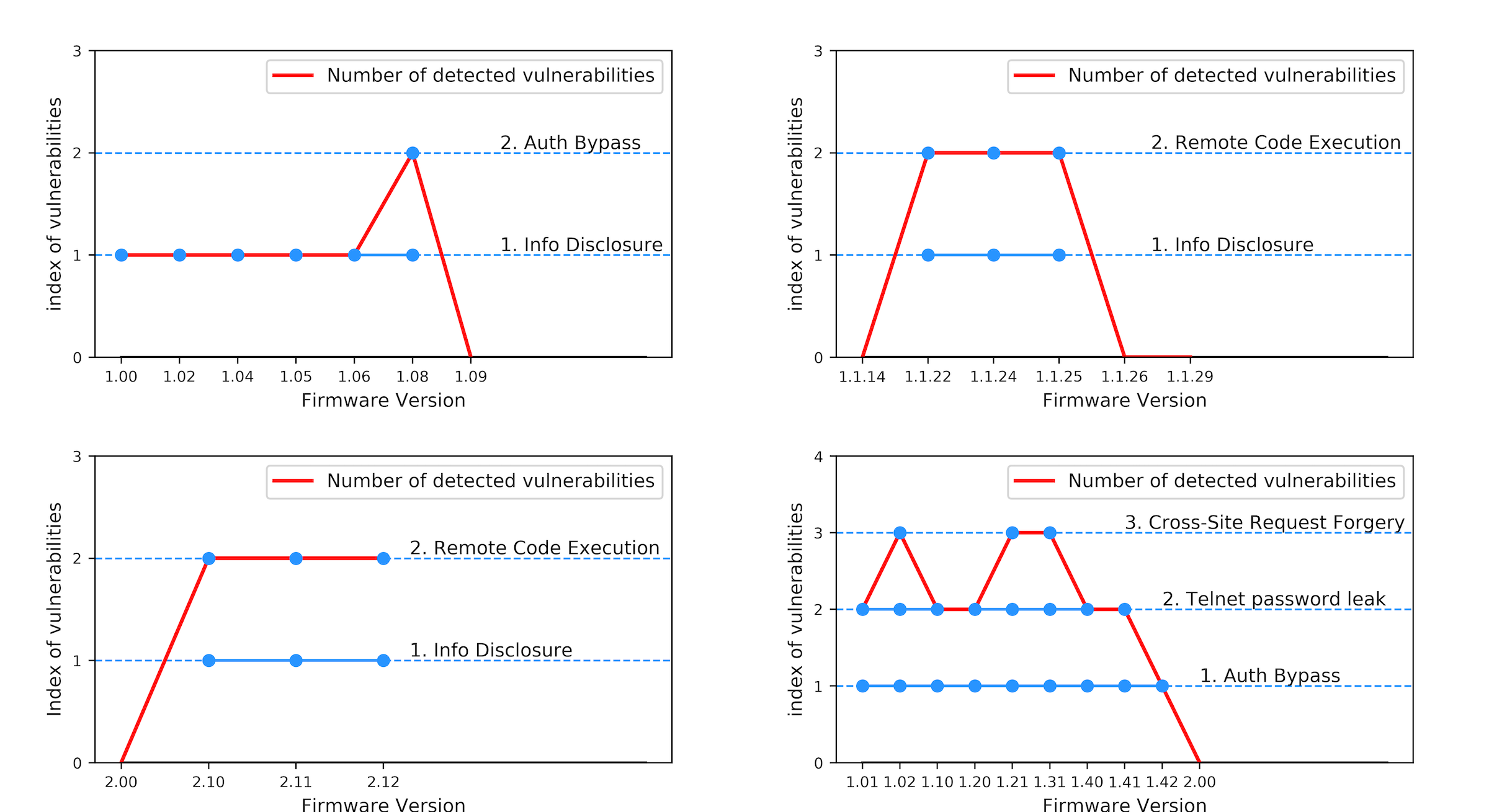
| Scientific Breakthrough | The existing commercial security testbeds, such as very famous IoT Inspector, are focus on the static analysis of the source code of the IoT devices. However, for those companies who want to test their product, revealing source code is risky and offering firmware binary is more reasonable. Moreover, by performing the firmware on the emulated system, our testbed could precisely trigger the suspicious file, capture the malicious behavior of the operation, and discover logic flaws, unknown and zero-day threats. The main breakthrough of this testbed is that we successfully operate 661 COTS firmwares (with brand Dlink, Zyxel, Netgear) on the emulated hardware architectures, such as ARM, X86, and MIPS. By exploiting public vulnerability testing tools, we found 115 vulnerable COTS IoT firmwares. |
||
| Industrial Applicability | For those IoT developing company without stronger security team, our testbed could offer an extensive vulnerability testing to their developed product and a corresponding testing report. The development teams could patch the vulnerabilities accordingly and make sure the product on the market is not vulnerable. For the company with individual security team, the testbed could be cooperated in the produce development cycle where the engineers could leverage this tool to examine the prototype of the product directly and fix the potential bugs in the next version. In both cases, the testbed improves the development quality from the perspective of security and significantly reduce the high cost of handling hacked or intruded IoT devices. |
||
| Keyword | Commercial IoT device Device Virtualization Dynamic analysis Firmware inspection Fuzzing Hardware emulation IoT malware IoT security security testbed vulnerability testing | ||
- smcheng@mail.ntust.edu.tw
other people also saw