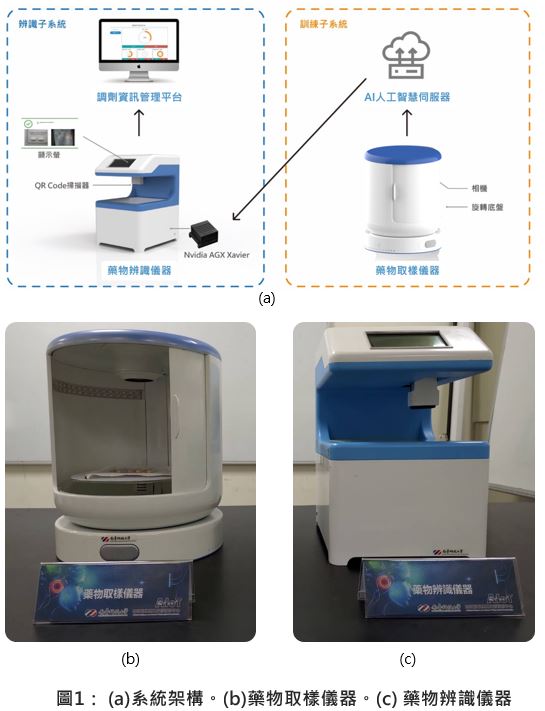
| Technical Name |
利用機器學習分析惡意流量特徵 |
| Project Operator |
Taiwan Information Security Center at National Chung Hsing University |
| Project Host |
王行健 |
| Summary |
The network technology plays an important role in the industrial control systems (ICS)then has become the target of cyber-attackers. For industrial internet-of-things (IIoT) applications with limited computing resources, designing an effective NIDS is challenging. A compacteffective NIDS for IIoT is proposedvalidated by using the more recent UNSW-NB 15 dataset to improve the detection capability against new types of attacks in the real world. Experimental results show that the proposed method achieves better performance than previous methods.
|
| Scientific Breakthrough |
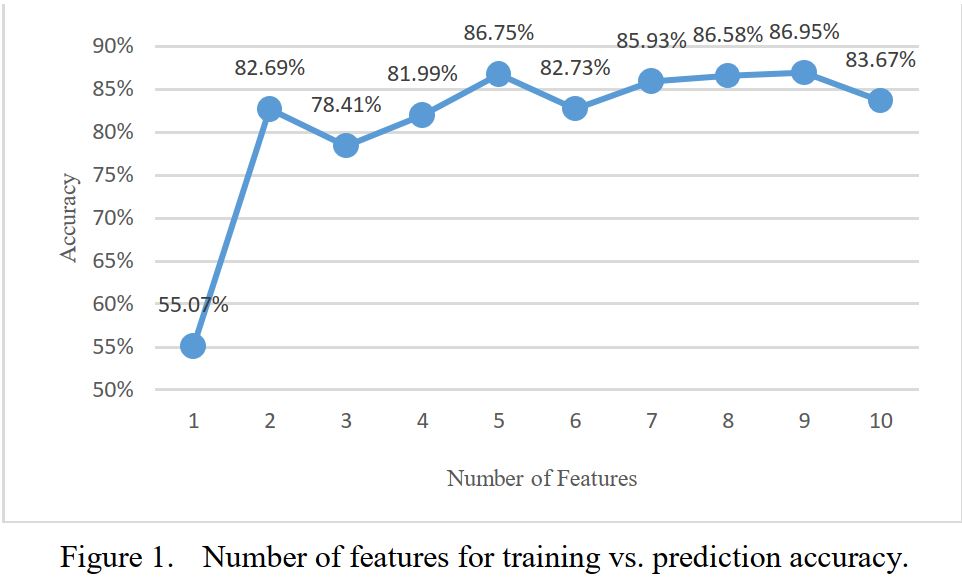
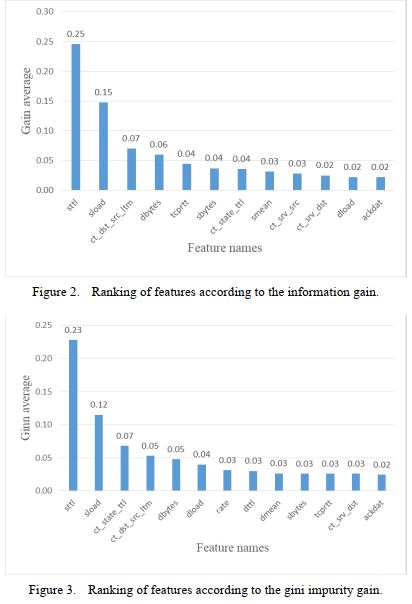
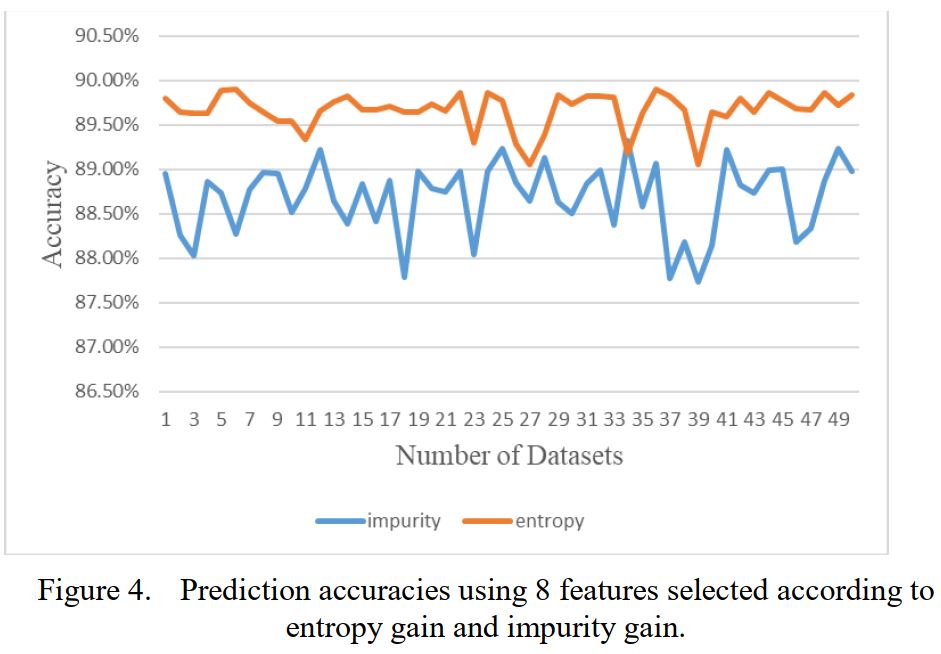
Our goal is to develop a machine learning based IDS that achieves the best overall performance targeted for UNSW-NB 15 dataset [5]. We will then show that the proposed scheme is also valid for traditional KDD-CUP-99 dataset. The proposed scheme is carried out in two phases. Phase 1 is to select the best combination of features that produces the best performance. In the second phase, multiple ML algorithms are evaluatedthe best one for this specific problem is selected. The dataset has to be pre-processed before these steps otherwise the results will be adversely affected.
|
| Industrial Applicability |
Intrusion detection systems (IDS) provide a feasible counter-measure against cyberattacks. The scale of internet grows exponentially in the last few decades. At the same time, new types of cyberattacks have been evolved over time, which implies that a successful IDS has to adapt to evolving attacks. Traditional IDS methods are signature-based, in which known malicious attacks are stored in database. Incoming network packets are compared to signatures logged in the database to determine whether they are cyberattacks.
|
| Matching Needs |
天使投資人、策略合作夥伴
|
| Keyword |
anomaly detection system internet of things machine learning cyber security |