| Technical Name | High Interactive Industrial Control System Security Protection Mechanism | ||
|---|---|---|---|
| Project Operator | National Cheng Kung University | ||
| Project Host | 李忠憲 | ||
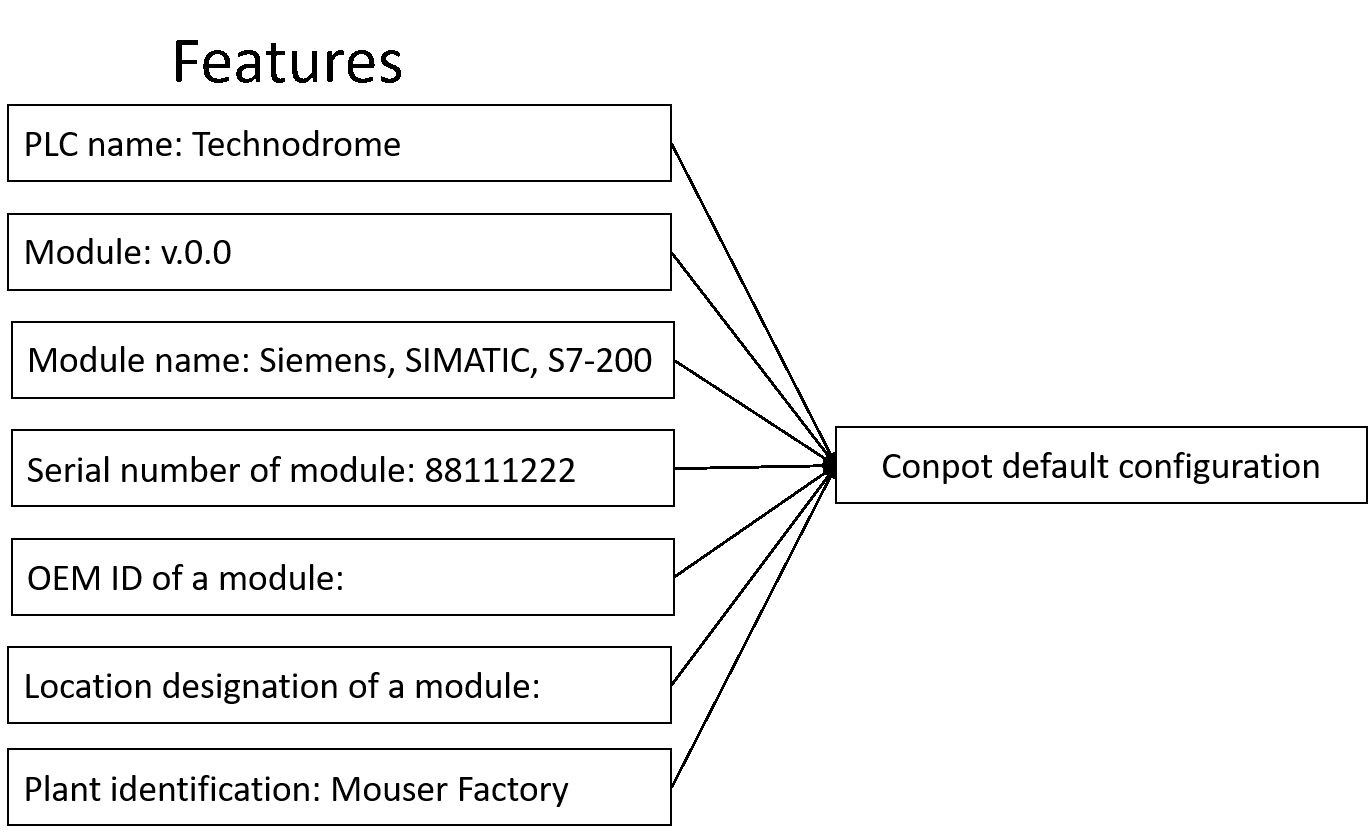
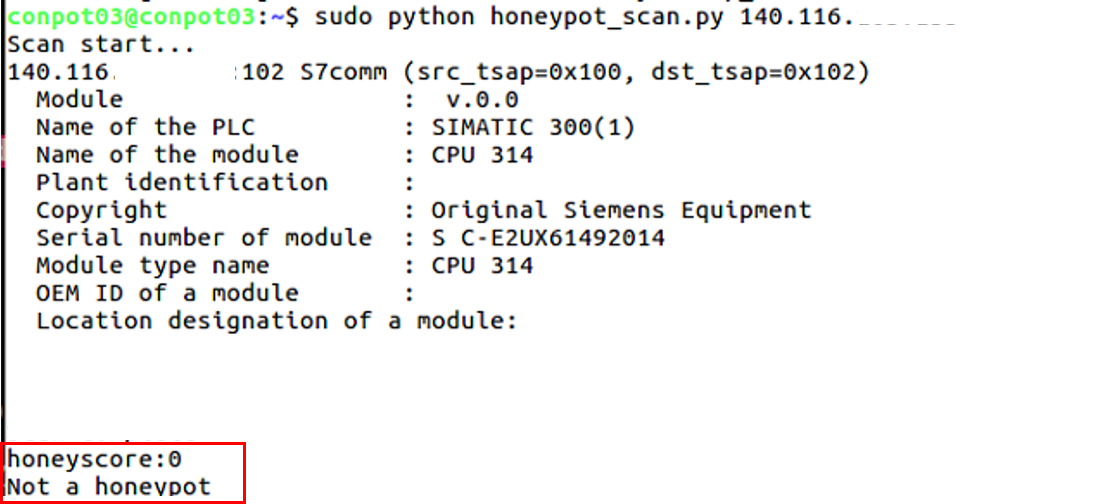
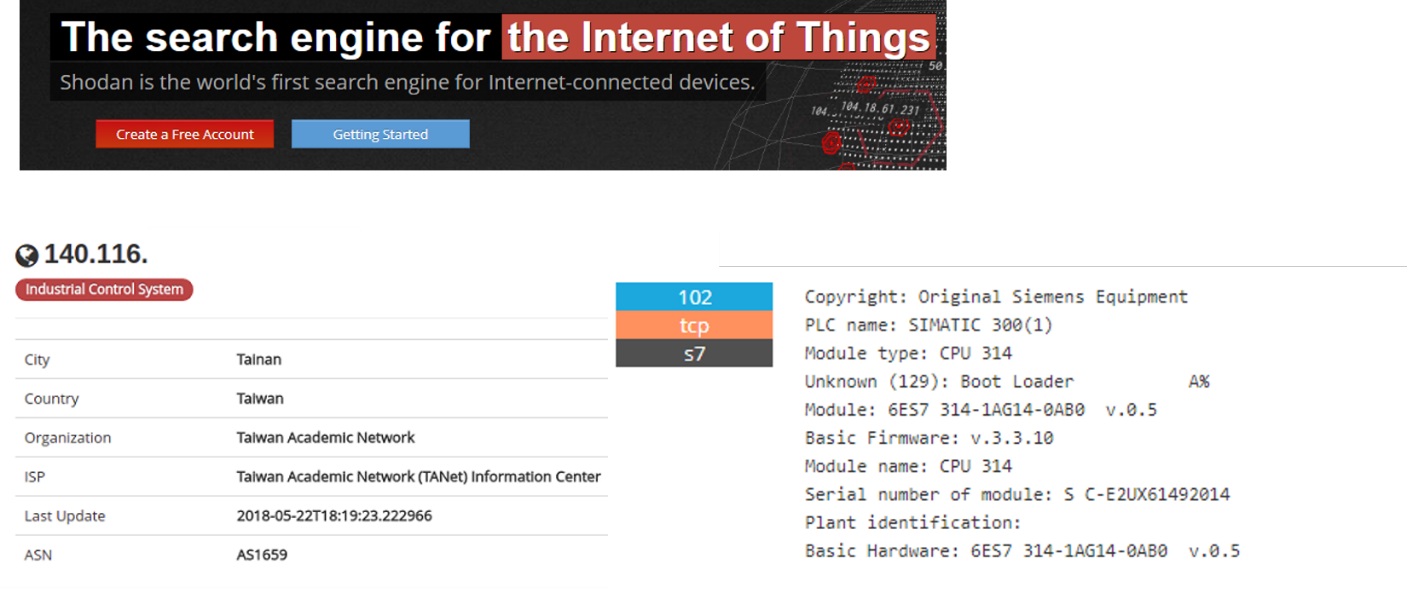
| Summary | Due to the negligence of the operators or the deliberate intrusion of the hackers, attackers could attack the industrial control equipment directly from the internal industrial network. To avoid the situation that the system is attacked by the attackers but is not aware of it, and further understand how the attackers initiate attacks to the industrial control equipment. the conpot been set in an industrial environment. We use the Conpot honeypot to disguise as an industrial control device to trap the attackers, but hackers can use the IoT search engine Shodan to find the attackable industrial control target and judge the fake device camouflaged by Conpot. The attackers can avoid attacking these honeypots and make the honeypots lose the trapping effect. Therefore, we analyze the way the search engine judges and change the honeypot configuration to achieve the trapping effect. |
||
| Scientific Breakthrough | This research is to improve the security of industrial control systems. After researching industrial control system related attack events and defense methods, designing an anti-detection mechanism supplemented by different simulation ratios to generate its system specifications and proceed accordingly Respond. In addition, for the test of overload and crash, the threshold is set, and the simulation stops responding, so as to simulate the industrial control system more realistically, and can actually convert safe commands to the actual system for operation. |
||
| Industrial Applicability | The industry providers that this technology can provide are as follows: 1. Antivirus providers, such as Symantec, Trend Micro, etc. 2. System providers, such as Microsoft, IBM, Apache, etc. We can help these enterprises protect the security of internal systems. |
||
| Keyword | Industrial Control System Industrial Security Honeypot PLC Shodan Network attack Critical Infrastructure Cybersecurity Netwrok Isolation sandbox | ||
- tsca@twisc.ncku.edu.tw
other people also saw