| Technical Name | Data Leakage Detection for Health Information System based on Memory Introspection | ||
|---|---|---|---|
| Project Operator | National Chiao Tung University | ||
| Project Host | 謝續平 | ||
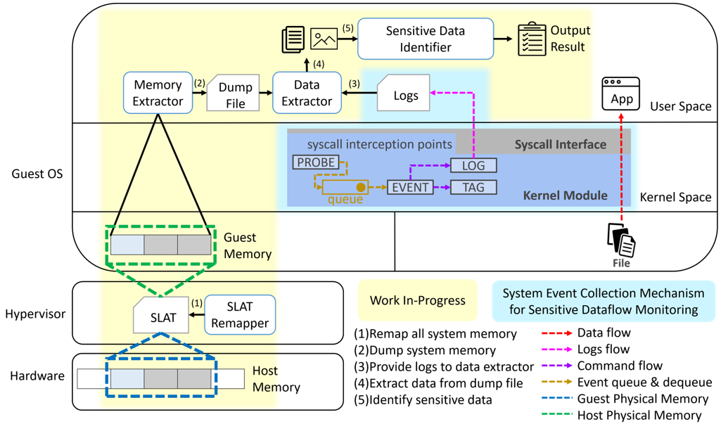
| Summary | In light of the rising need for more effective data loss prevention, we propose a novel data leakage detection system based on memory introspection and pattern recognition. The proposed system is robust against transport layer encryption such as Transport Layer Security (TLS)/Secure Sockets Layer (SSL) and at-rest data encryption such as disk or file encryption. By examining the raw contents in the memory directly, the system is largely message format-agnostic, thereby is compatible with different types of custom software. |
||
| Scientific Breakthrough | Hypervisor-based System Memory Snapshot |
||
| Industrial Applicability | Tracking the flow of sensitive data is very important for both government agencies and corporates. Following the implementation of the Personal Data Protection Act, businesses at any level and of any type all have to pay attention to the management and protection of personal data. The proposed technology can be materialized through various channels including IT equipment vendors, cybersecurity companies, or system integration companies. |
||
| Keyword | Data Privacy Data Loss Prevention Memory Inspection Electronic Health Record Health Information System Virtualization Neural Networks Pattern Recognition GDPR Security | ||
- cchingyi@nctu.edu.tw
other people also saw